Well after a large ordeal and time spent out of love, I co-authored a
Well after a large ordeal and time spent out of love, I co-authored a
My Projects and Written Articles
Find out more about me through my current project involvement, past projects and articles.
Well shocking to some, I eventually became a co-founder of a successful services startup and leading a team while tending to the needs of a company.
Here is a paper I was attempting to publish through ACM, but was primarily denied due to having to use proxies in-order to gain information from Bugzilla. Secondly, the reviewers didn't understand the issues around stackoverflow for companies and how this could be used intandem with web-proxies or browsers to warn developers etc... oh well - so here is to my blog for open publishing.
This exploratory study involves the examination of the relationship between online community forum posts to referenced open-source projects and calls attention to the software quality inherited by implementing associated project code. To deduce potential risk for a developer utilizing an online resource, over five million posts were filtered out from a large Stack Overflow (SO) data-mining experiment and examined for similarities, relationships and risk related to a popular opensource project.
The study presents a unique approach which utilizes extracted traditional software quality and change metrics from a selected project, combined with project association indicators to create an aggregate score for potential software quality risk. Resulting information suggests that determining relationships when evaluating software quality risk from incomplete source code snippets is difficult, but not impossible. In general, the study discovered that minimal-to-moderate risk was identified for snippets with an established relationship to the GTK+ project and no snippets found related to highly-to-extremely risky sourcecode.
Presented two full-length talks running approximately 45 minutes each; one for using OpenWRT in embedded projects which includes licensing and build-root navigation. The second, was a high-level discussion on how one goes about deep packet inspection in user-space with a brief tour of industry technology and a protocol example (FTP).

Audience numbered greater than 35+ and ranged from intermediate skill-levels to semi-advanced (in their own fields). The questions were numerous, well-directed and overall, the event was a large success.
I was scouting through my NAS and discovered, I still had a copy of all of my slide decks discussing a basic introduction to computer and network security. Projects and labs included.
This course introduces students to the essential concepts surrounding information technology security. Topics include operating system and network vulnerabilities, web application security, cryptography, password management and access control, as well as business-related topics such as disaster recovery and risk management.
Excerpt from my paper
Cryptography is an age old form of disguising and protecting communication which was used by individuals, armies and organizational communiques. In the early days of mankind’s history, cryptography was fairly simple according today’s standards, but skyrocketed forward with the electronic evolution which enabled new ideas and solutions. One early example of cryptography was Julius Caesar’s usage of a simple algorithm to encrypt messages for his field generals to reduce the potential of voluntary or involuntary information leaks by messengers [Uni14]. In effect, Julius Caesar was attempting to reduce side-channel attacks again his messages by removing the messengers from the main communication channel.
A side-channel attack is defined as any attack based on information gained from the implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms through cryptanalysis. Often attacks are limited to physical implementations, but recent critical vulnerabilities exploit flaws such as Heart Bleed [CVE14] suggest a focus on the implementation of algorithms and protocols in order to reduce the difficulty of breaking secured communications.
This paper will explore possible avenues of bypassing cryptosystem security through side-channel attacks through invasive and non-invasive vectors.
Well its been a little while since I got my creative juices flowing, but here is an interesting little concept that will be replacing an ancient solenoid controller in the sugar shack. So what is it and what does it do?
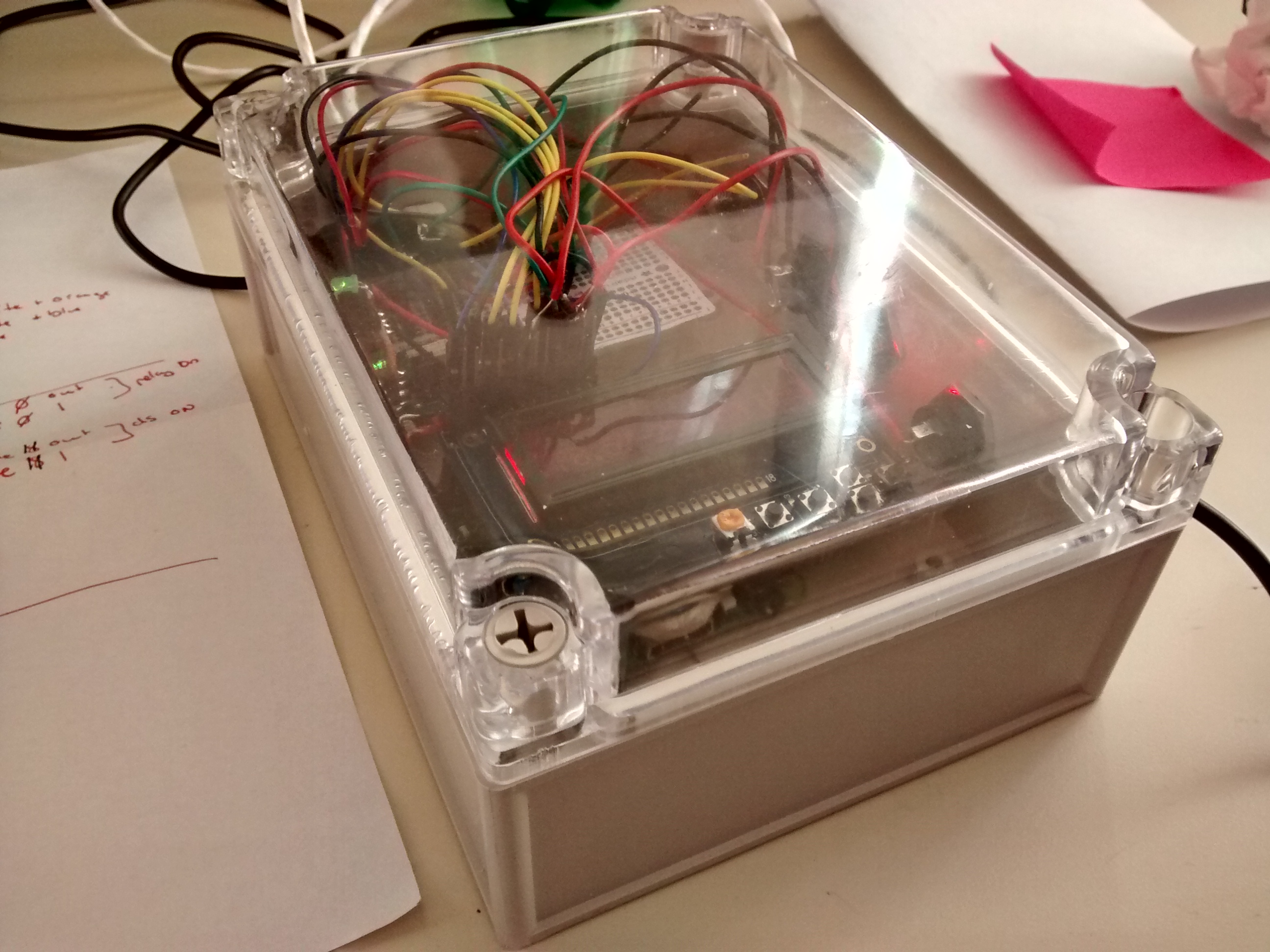
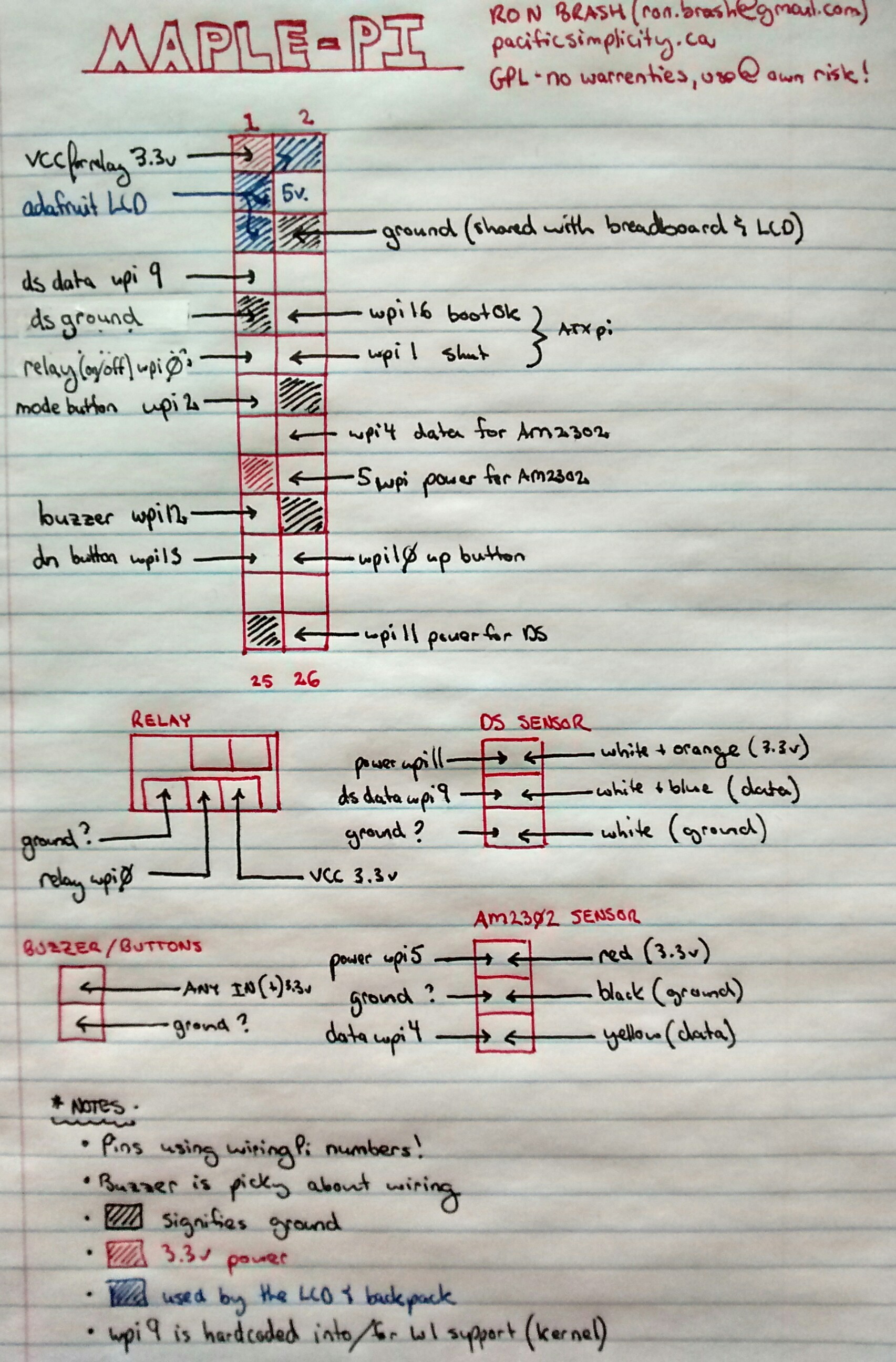
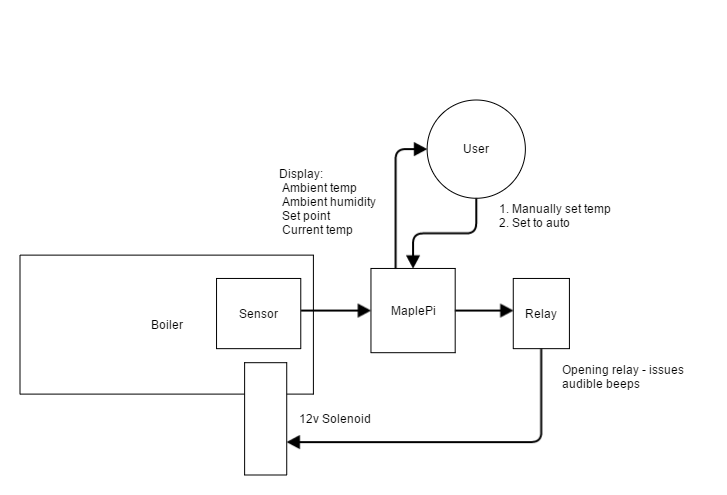
This little computer is running Linux (OpenWRT actually) to control an electric solenoid through a relay that is activated when the boiling maple syrup reaches a user-set temperature threshold (~219.20f default). The idea is that once you have manually determined what temperature produces the correct consistency of syrup, you can now automate the valve on the boilers to pour out the "cooked" syrup. When the temperature goes down because of the addition of new maple water, the solenoid closes. Simple right?
The device isn't entirely complete - GPIO for buttons is too slow (you have to hold them down). Later revisions, I suspect will be able to determine the correct consistency of the syrup using humidity and conductivity data.
What parts are required?
Here is my shopping list:
- 4 push buttons (I used 2 green, 1 yellow and 1 red)
- ATXraspi
- Misc wires, solder, connectors
- RaspberryPI A+/B+
- SparqEE Relay
- Adafruit LCD+backpack for raspi
- AM2302 temperature and humidity sensor
- DS18B20 high-temp waterproof sensor
- Food safe heat shrink to wrap the DS18B20 sensor
- SD card adapter and micro-SD card
- ~4.7K-10K resistor for the DS18B20
- Water-proof case and wire glands
Maple-Pi Pinout
The General Concept
 Once again, I am on the podium speaking about Linux and all of the troubles/wonders when using it. We discussed how to use OpenWRT, some of the problems you will encounter during the development of a generic embedded product, questions you will have to ask yourself and of course - licensing!
Once again, I am on the podium speaking about Linux and all of the troubles/wonders when using it. We discussed how to use OpenWRT, some of the problems you will encounter during the development of a generic embedded product, questions you will have to ask yourself and of course - licensing!

 Found and merged laboratory code to create a more recent location for any AMT work by Concordia university with permission of the original creators at UT of Dallas Automatic Multicast Without Explicit Tunnels.
Found and merged laboratory code to create a more recent location for any AMT work by Concordia university with permission of the original creators at UT of Dallas Automatic Multicast Without Explicit Tunnels.
 Well I finally finished my merger of an insane amount of derelict code to the monolithic project OpenDiameter. Unfortunately, I could not obtain the rights to actually create a new package, but the SVN is updated with the latest code including an OpenSSL patch.
Well I finally finished my merger of an insane amount of derelict code to the monolithic project OpenDiameter. Unfortunately, I could not obtain the rights to actually create a new package, but the SVN is updated with the latest code including an OpenSSL patch.
In truth, I am extremely thankful for this project, but humbly tired and ready to move onto another. Here is why, despite many lessons learned: